In an increasingly digitalized world, where customer data is the lifeblood of service-oriented businesses, ensuring its security and confidentiality is paramount. Customer Relationship Management (CRM) systems serve as the backbone of many service providers, managing interactions with current and potential customers. However, the rise in cybersecurity threats highlights the need for robust data protection measures. This paper delves into the significance of End-to-End Encryption (E2EE) in Pixie CRM systems for service providers, examining its benefits in enhancing data security, ensuring regulatory compliance, fostering customer trust, mitigating insider threats, protecting against external attacks, and preserving confidentiality.

Maximizing Security and Trust: The Role of End-to-End Encryption in CRM Systems for Service Providers
1. Introduction:
1.1 Background:
The evolution of digital technologies has revolutionized the way businesses interact with their customers. CRM systems play a pivotal role in managing customer relationships, streamlining processes, and driving business growth. However, the increasing frequency and sophistication of cyber threats pose significant challenges to data security and privacy.
1.2 Purpose:
This paper aims to explore the importance of E2EE in CRM systems for service providers, elucidating its benefits and implications for enhancing data security, regulatory compliance, customer trust, and confidentiality.
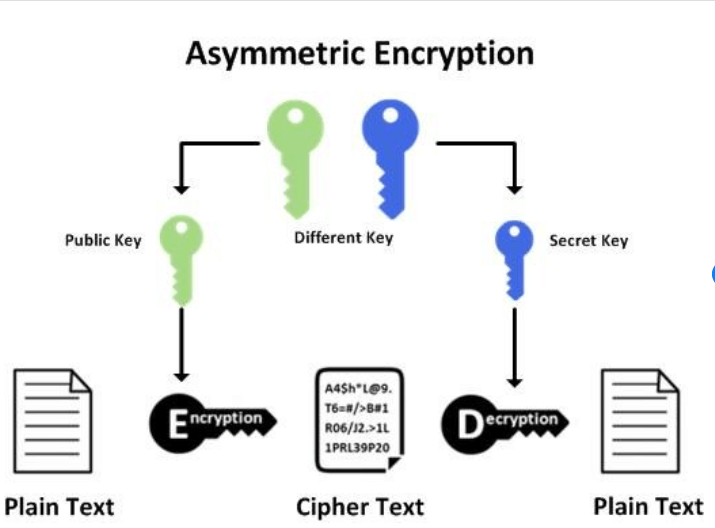
2. Understanding End-to-End Encryption:
2.1 Definition and Principles:
E2EE is a cryptographic technique that ensures data remains encrypted throughout its entire lifecycle, from sender to recipient. Unlike traditional encryption methods, where data is decrypted at intermediary points, E2EE guarantees that only authorized parties possess the keys necessary for decryption.
2.2 Mechanisms and Implementation:
E2EE employs robust encryption algorithms, such as AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman), to protect data in transit and at rest. Implementation involves generating unique encryption keys for each user, thereby minimizing the risk of unauthorized access.
3. Benefits of E2EE in CRM Systems for Service Providers:
3.1 Enhanced Data Security:
E2EE mitigates the risk of data breaches and unauthorized access by encrypting customer data end-to-end. This ensures that even if a malicious actor gains access to the CRM system, they cannot decipher sensitive information without the requisite encryption keys.
3.2 Regulatory Compliance:
In industries governed by stringent data protection regulations, such as healthcare (HIPAA), finance (PCI-DSS), and general data protection (GDPR), compliance is non-negotiable. E2EE helps service providers adhere to these regulations by safeguarding customer data against unauthorized disclosure and ensuring confidentiality.
3.3 Fostering Customer Trust:
In an era characterized by data privacy concerns and heightened awareness of cybersecurity risks, earning and maintaining customer trust is vital. E2EE demonstrates a commitment to data security and privacy, instilling confidence in customers that their sensitive information is adequately protected.
3.4 Mitigating Insider Threats:
Insider threats pose a significant risk to organizational security, as employees with access to sensitive data may abuse their privileges or inadvertently compromise data integrity. E2EE limits the scope of insider threats by restricting access to encrypted data, thereby reducing the likelihood of unauthorized disclosure or misuse.
3.5 Protecting Against External Attacks:
External cyber threats, ranging from phishing attacks to ransomware campaigns, continue to pose a significant challenge to service providers. E2EE serves as a robust defense mechanism against such threats, as intercepted data remains unreadable without the encryption keys, thwarting potential exploitation by malicious actors.
3.6 Preserving Confidentiality:
Confidentiality is paramount in industries where sensitive information, such as legal documents, medical records, or financial transactions, is exchanged. E2EE ensures that data remains confidential throughout its transmission and storage, safeguarding proprietary information and preserving client confidentiality.
4. Challenges and Considerations:
4.1 Key Management:
Effective key management is critical to the success of E2EE implementation. Service providers must devise robust key management strategies to secure encryption keys, prevent unauthorized access, and facilitate key rotation and revocation when necessary.
4.2 Performance and Scalability:
While E2EE offers unparalleled security benefits, it may incur performance overhead, particularly in resource-constrained environments or high-volume transactional systems. Service providers must strike a balance between security and performance to ensure optimal system functionality and scalability.
4.3 Usability and Accessibility:
The usability of E2EE-enabled CRM systems is contingent upon user awareness, training, and adoption. Service providers must prioritize user experience and accessibility while implementing E2EE, minimizing disruptions to workflow and ensuring seamless integration with existing processes.
5. Case Studies and Best Practices:
5.1 Healthcare Industry:
Healthcare organizations leverage CRM systems to manage patient relationships, appointments, and medical records. E2EE plays a crucial role in safeguarding patient confidentiality, ensuring compliance with HIPAA regulations, and protecting against data breaches.
5.2 Financial Services Sector:
Financial institutions rely on CRM systems to manage client portfolios, facilitate transactions, and analyze market trends. E2EE enables secure communication between financial advisors and clients, mitigates the risk of financial fraud, and enhances regulatory compliance.
6. Future Trends and Emerging Technologies:
6.1 Quantum-Safe Encryption:
The advent of quantum computing poses new challenges to traditional encryption algorithms. Quantum-safe encryption algorithms, such as lattice-based cryptography and quantum key distribution (QKD), offer promising solutions to mitigate the threat of quantum attacks on E2EE systems.
6.2 Homomorphic Encryption:
Homomorphic encryption allows for computations to be performed on encrypted data without the need for decryption, preserving data privacy while enabling data analytics and machine learning. Integration of homomorphic encryption into CRM systems holds potential for enhancing data security and utility.
7. Conclusion:
In conclusion, E2EE represents a cornerstone of modern data security practices, particularly in Pixie CRM systems for service providers. By leveraging E2EE, service providers can enhance data security, ensure regulatory compliance, foster customer trust, mitigate insider threats, protect against external attacks, and preserve confidentiality. However, successful implementation requires careful consideration of key management, performance considerations, usability concerns, and emerging trends in encryption technologies. As the digital landscape evolves, service providers must remain vigilant and proactive in adapting their security strategies to mitigate emerging threats and safeguard customer data.
End-to-end encryption (E2EE) in Customer Relationship Management (CRM) systems for service providers offers several key benefits:
Enhanced Data Security:
E2EE ensures that data is encrypted from the moment it leaves the sender's device until it reaches the intended recipient's device. This prevents unauthorized access to sensitive customer data, such as personal information, financial details, and communication logs.
Regulatory Compliance:
Many industries, such as healthcare (HIPAA), finance (PCI-DSS), and general data protection (GDPR), have strict regulations regarding data security and privacy. Implementing E2EE helps service providers comply with these regulations by ensuring that customer data is adequately protected.
Customer Trust and Confidence:
E2EE provides customers with assurance that their data is secure and private, fostering trust and confidence in the service provider. This is particularly important in industries where confidentiality is paramount, such as legal services, healthcare, and financial services.
Mitigation of Insider Threats:
E2EE minimizes the risk of insider threats by limiting access to customer data to only authorized parties. Even if a malicious insider gains access to the CRM system, they would be unable to decrypt and access sensitive information without the necessary encryption keys.
Protection Against External Threats:
E2EE also safeguards customer data from external threats, such as hackers and cybercriminals attempting to intercept communications or gain unauthorized access to the CRM system. Even if an attacker manages to compromise the system, the encrypted data remains unreadable without the encryption keys.
Preservation of Confidentiality:
Service providers often deal with confidential information shared by their clients. E2EE ensures the confidentiality of this information by preventing anyone other than the intended recipient from accessing the data, including the service provider itself.
Overall, implementing E2EE in Pixie CRM systems for service providers not only enhances data security and compliance but also helps build trust with customers and protects sensitive information from both internal and external threats.